A new age of phishing attacks that utilize spam to disperse web links to phishing sites were actually located to be put up and also organized on the personal computers of property broadband consumers. Such a brand new trend called as ‘Phish@Home’ was actually seen in the 1st sector of 2014 through PhishLabs – a leading service provider of cybercrime protection as well as intelligence information companies. What are our experts speaking about …hydra tor
By browsing the household solution IP address space, attackers capitalize on people that have (1) permitted the distant desktop computer protocol (RDP) service on Microsoft Windows and (2) make use of an unstable password. The enemies then put up PHP Triad (totally free, open-source, internet server software program) as well as publish a number of different phishing pages. Hyper-links to the phishing websites (often banks and also payment web sites) are actually delivered via spam email information.

This style is extremely notable, as phishing web sites held on weakened individual personal computer are more likely to possess a much longer life-span than those located in a conventional organizing atmosphere. (The holding service provider’s regards to solution generally enable them to swiftly stop destructive websites; Internet service providers (ISPs), on the other hand, have little command over customer-owned home computers connected to the ISP through non commercial broadband networks.)While RDP is actually shut down through default on desktop computers with modern-day versions of Windows, it was found that the many individuals still make use of RDP as a free, no 3rd party method to from another location access at-home units.
Depending on to the record, a few of these recent phishing assaults advised “evidence of social planning to get the consumer to make it possible for RDP or produce Remote Aid invitations; deeds with shellcode or even malware that enables RDP; or attacks that target various other feasible weak spots in RDP arrangements including Restricted Admin method in RDP 8.1.” In every strike examined, opponents got only by means of Weak passwords and also rdp-enabled connections.
Why Worry?
These strikes target domestic units, the goals of the enemies can not be forecasted. Productive development of such a system of risked equipments could bring about a big crawler system which could be utilised for larger strikes or violations. Maybe additionally used to send out spam email or even join dispersed denial-of-service attacks.
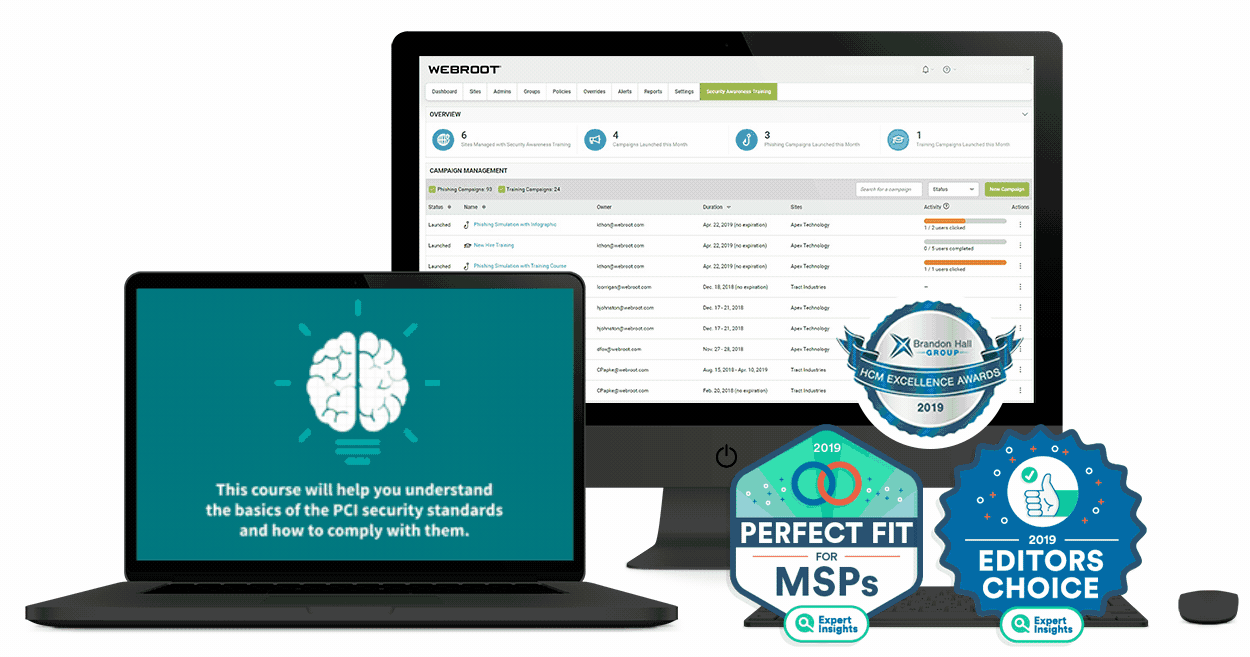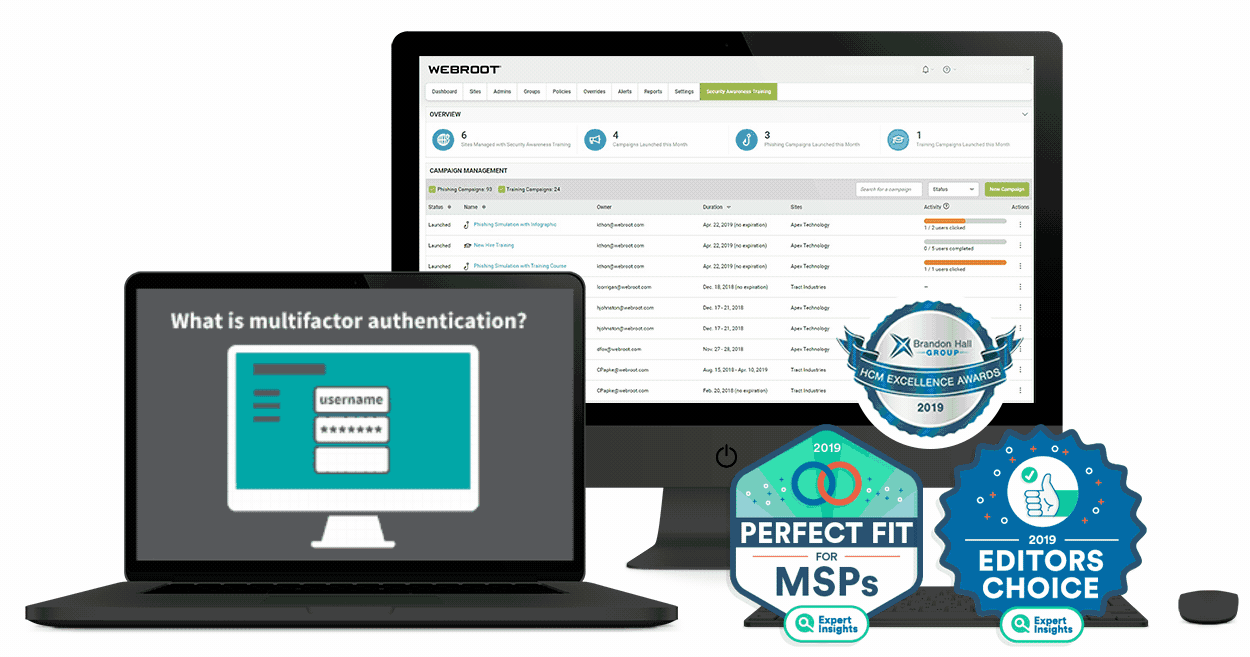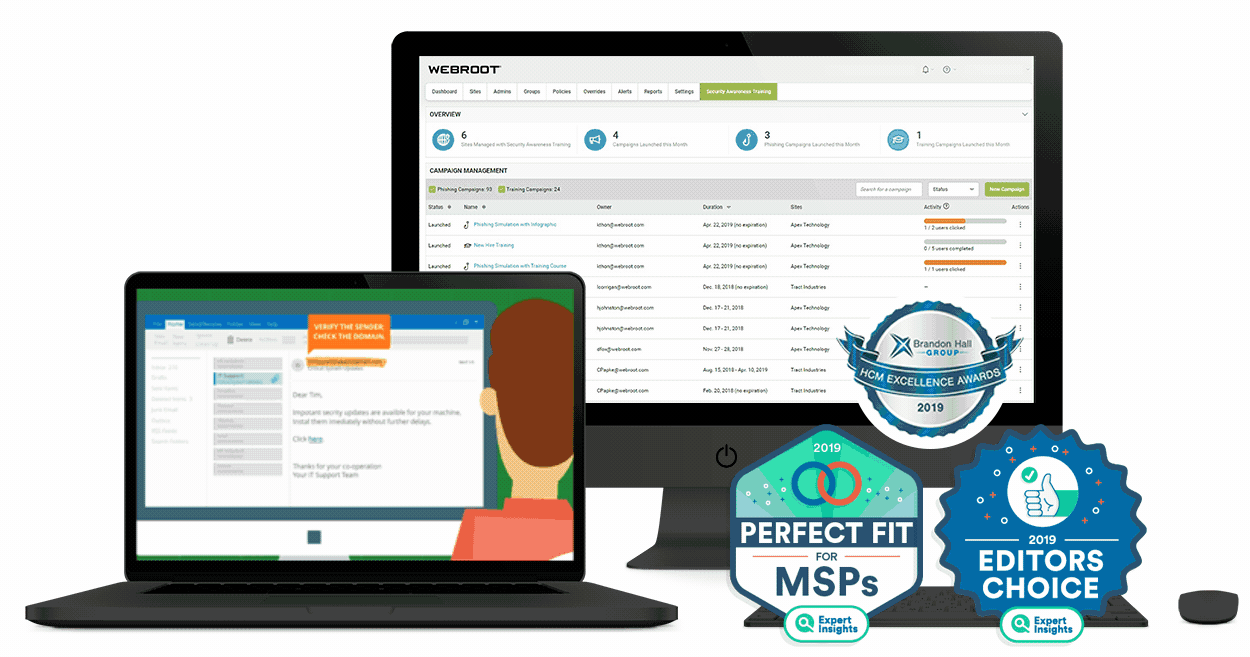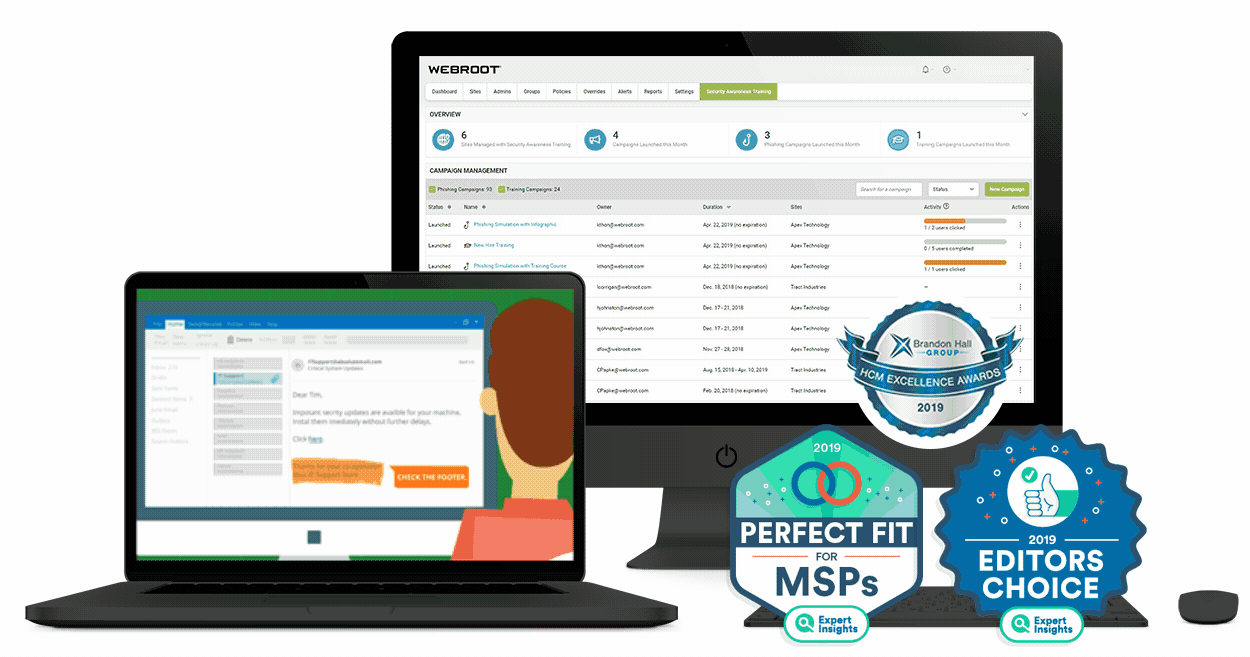
Such celebration plainly indicate the need for protection for house tools, owing to the advancement of Net of Factors. There exists a growing demand for surveillance services for property tools, besides the overall workplace devices, as the level of threat and also quantum of susceptibility is similar, irrespective of whether the tool resides at home or in your office system. Such a series of assault precisely suggest the requirement for surveillance of house tools.

